
A New Exhibition Celebrating Is Coming to New York
Lorem ipsum dolor sit amet,sed diam nonumy eirmod tempor invidunt ut labore et dolore magna…
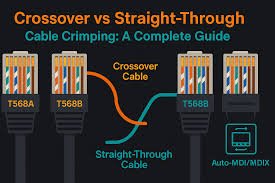





Straight-through cables connect different device types (e.g., PC to switch) using the same wiring standard T568B/T568Bcap T 568 cap B / cap T 568 cap B𝑇568𝐵/𝑇568𝐵) on both ends. Crossover cables connect similar devices (e.g., PC to PC) by swapping transmit/receive pairs (T568A/T568Bcap T 568 cap A / cap T 568 cap B𝑇568𝐴/𝑇568𝐵), allowing direct…

Configuring a Cisco switch involves moving through specific management modes to establish basic identity, security, and connectivity. 1. Establish Physical Connection Connect your computer to the switch’s Console port using a rollover (console) cable. 2. Access Management Modes Once connected, you will see the Switch> prompt. Use these commands to enter configuration modes:

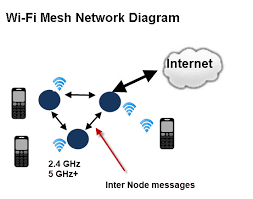
Setting up a mesh WiFi network is generally a user-friendly process that can be completed in about 30 minutes using a smartphone app. Unlike traditional routers, mesh systems use multiple nodes to create a single, unified network throughout your home. 1. Initial Hardware Setup: 2. Configuration: 3. Strategic Node Placement: 4. Adding Satellite Nodes: 5. Final Optimization: These…

To add a CP Plus camera to a Hikvision NVR, you must use the ONVIF protocol, as they are different brands. Follow these steps to ensure a smooth connection: 1. Initial Camera Setup (CP Plus Side) Before adding the camera to the NVR, you must configure it using its web interface or the CP Plus Config Tool. 2. Configure the…

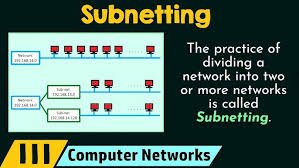
Subnetting is the process of dividing a single large IP network into multiple smaller, logical sub-networks called subnets. Core Concepts Formulas Step-by-Step Example Scenario: You have the network 192.168.1.0/24 and need to divide it into 4 equal subnets. Benefits of Subnetting

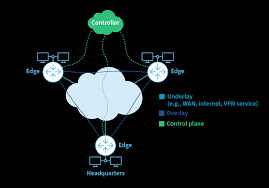
SD-WAN (Software-Defined Wide Area Network) is a virtualized networking approach that uses software to manage and optimize connectivity between geographically dispersed locations, such as branch offices, data centres, and cloud environments Core Components Key Features

A firewall serves as a company’s first line of defense, providing essential network security by monitoring, filtering, and controlling incoming and outgoing traffic based on security rules. It acts as a barrier to block unauthorized access, malware, and cyberattacks, while protecting sensitive data, ensuring regulatory compliance, and enabling secure, monitored remote access. 1. Network Access…

Trends in Data Center Infrastructure On-premises facilities provide organizations with comprehensive control over their data environments, allowing for tailored security, customization, and management. However, the significant financial investment required for construction, ongoing maintenance, and scalability has led to a notable decline in their prevalence. According to the Uptime Institute’s projections for 2025, more than fifty…

IT incidents are like uninvited guests at a party – disruptive, unwelcome, and demanding immediate attention. But unlike uninvited guests, IT incidents can’t be politely ushered out the door. They require a well-orchestrated response, a dance of swift action and meticulous procedure. Here’s how to tango with IT incidents and emerge victorious. When IT Glitches…

Networks are the silent heroes of our digital world, powering everything from the local printer in your office to the vast expanse of the internet. But have you ever stopped to wonder how they actually work? Let’s dive into the fascinating world of network communication and unlock its secrets. The Building Blocks: Devices: The stars of…